The latest version of Firefox has been released, and it really is a major upgrade with lots of really useful new features, including a new sync and very impressive speed bump.
Just dug through old emails, we bought them from Amazon but yes they were shipped from China. For my most recent purchases, it's lucky that I'm not currently in France but out in the Middle East and the range of phones available is much improved from that available in the French countryside :-)
This link is to the retailer... http://goo.gl/xHOobk
Thanks Steve, where do you shop for them, ebay?
I ran a clone of the Note 3 phone for just over a year, believe it cost me around GBP99 delivered (so just over your pricing). All depends upon your usage desires, if for light 'phone' use then these are all capable of operating to expectations.
You'll probably not receive the latest version of Android and the processor/camera may well be of a spec lower than current mainstream offerings.
I'm currently running two Huawei phones, each around €120 but they are both dual-sim units and have 3g connectivity (4g would be nice as it is very fast here but that does mean buying a more up to date unit from the upper level of manufacturers.
Android Smartphones for under a 100 euros, anything worth looking at? Which of the Chinese brands perform well?
As I tweeted yesterday, this flaw in Microsoft IE is a serious one , and governments are noe urging people to switch to using Firefox or Chrome immediatley.
If you are using Windows XP, then you won't be getting a fix, so just turn off Flash plugin support if you are still using IE, or switch to another browser.
Government advise to switch from Using Microsoft IE until at least a fix is found.
Also, yet another good reason to consider your options with XP, this will be the first of many issues, that are just not going to be fixed.
Ha Ha Ha - Going back to the Heartbleed bug issue - I see that it is now reported that 'testing' of servers by third party websites are considered possibly illegal under the laws of both the UK and the USA http://goo.gl/jc1NtD
For those of us that utilise multiple pieces of hardware (desktop / laptop / mobile) then the question of keeping all the passwords in sync comes into the picture. I use Passpack which is not a downloaded/installed utility but is in the 'cloud'. Before the anti-cloud screams begin I do believe that their security (AES-256) is as good as the others available. Multiple steps are required to login to your account such as password, anti-robot step and finally a keyphrase which is used to 'decode' the password manager pack (this last stage they say is never transmitted to their servers, only you have it and god help you if you forget it as it cannot be regenerated/recovered).
@John Well, keepassx is a utility you download and run on your machine - so as long as it works with you machine, no need to worry about the company going out of business. Worth taking a look and seeing if you like it.
@Stuart I have used PWsafe for Windows many years ago, but it ties you into Windows. KeepassX is completely cross platform and works with Windows, Mac and Linux, so that's why I use it.
I’ve a load off passwords Nick and I’ve thought about using one of the password generation/storing products but I worried about what would happen if the company went wallop. I’ve started to try out the facility for Safari to generate/store passwords in Mac OS and IOS for a few non critical accounts but I would like one really secure centralised method of managing passwords as it is an ever increasing chore.
Anybody else use PWsafe? I use it for all my passwords and keep a seperate copy on a USB for OH use if something happens to me.
@Diana , sounds like you have a good password strategy - Lastpass orkeypassx could definitely help you look after themn securely.
@Shiela - that did make me smile ;-)
@Dorothy - I agree DD-WRT is a great way forward as you then have full control over distro and all the patches. I use Smoothwall.org for my security as I used to be part of the development team. Love your definition of a script kiddie - damned accurate. The real black hats I have respect for, script kiddies are nothing but pond scum.
@John I'm in complete agree - lets Keep Calm and Carry on ;-)
@vic - infosec - information security
Dorothy, This ain't no yellow brick road. Let's be Lion hearted, not scarecrows and just let the Tinman sort out any "vector of attack", just like he always does :-)
Comedian Nick Helm has won an award for the best joke of the Edinburgh Fringe.
The up-and-coming funnyman was given the prize by digital TV channel Dave, whose panel put a selection of their favourites to a public vote.
He won for the joke: "I needed a password eight characters long so I picked Snow White and the Seven Dwarves."
I used to train staff about passwords, I used to tell them that the password should be at least 9 characters, mixed cases, alpha-numeric, not spelling real words or dates, never written down. I would then say I knew full well that if they followed all the rules they'd never manage to sign in. However, finding a "good" password and never changing it is unwise. Somewhere in the middle is a reasonably safe route: find a combination of letters and numbers and modify it regularly, ideally monthly because it becomes routine.
So how am I reacting to the latest scare? I'm not too worried. I have a large file of ids and passwords, and they are changed less often than my office ones were. If the hackers have already intercepted my id and password (which is very unlikely indeed) then they are probably out of date. I will only find out if they try to use it to commit fraud, and I don't expect them to do so.
I should mention that IT problems are usually known to the industry first,then the trade press, long, very long, before they are reported by the mainstream press, and the last to report them is usually the BBC.
Remember the Millenium Bug, so widely publicised, so many scare stories, utter bunkum? Not entirely, spouse spent two years leading a team correcting systems dealing with life insurance policies. It did matter, it had to be done, and it worked, but real life bore little resemblance to what we read in the papers. Press releases like this sell security services and systems and play on the understandable fears of the vast majority of the public whose areas of expertise lie elsewhere. It is a good reminder of the need for all of us to protect our own data and not take risks.
Finally, if a hacker wants to cause havoc, they will do better by obtaining the records of a company with millions of customers, rather than by hacking the accounts of millions of individuals who have few accounts in common, many of whom are likely to be broke!
My opinion only, all grown-ups can make up their own minds.
Vic, how about you and I rewrite it all like Officer Crabtree might speak it in 'Allo 'Allo. Then we give it to a French mate to translate on. We will not understand a single word, but by golly we'll have fun :-D
Really you blokes, for as many years as I have stuck my head in using the technology, including the full 26 years of the web and all, I also prefer plain language. I have known quite a few people who worked on Silicon Fen developing things we can only dream of, but even as total boffins they used civilian speak to mere mortals.
Dorothy, all the major network component people are already deploying fixes, where they might be needed, F5 , Cisco etc. I think everyone in the industry is checking and applying fixes.
If you are worrying about your home router, well to be honest there are probably many issues around them, as all my routers never seem to get patches for anything, so they live with what they were supplied with. However, make sure you don't expose the web interface to the internet. It should only ever be exposed to the internal subnet - thus the potential for exploiting this ssl exploit is then zero.
The router should be locked down to the bare minimum to get your work done, and nothing should be allowed through it you can't monitor.
You mis-understood what I meant about being trivial - it is now, as engineers have had time to look at it - and the security team that found it , should have kept their mouths shut until the fixes had been built - which is normal practice.
Prior to this though, only a much smaller number of people would have been able to use it, thus the major exploits would have already taken place.
Virtually all the sites I use have already been patched, and I have changed my passwords, so it makes sense to pursue the fix and getting things sorted, and we can concern ourselves with stopping it happening again later. Also many large sites are confirming they are not affected at all.
No one is taking this lightly, but it has to be seen in proportion. Lots of software have bugs, and I'm far more worried about the millions of people still using Windows XP now with zero security updates. They truly are a script kiddies paradise
What about my reassurance Vic. I’m offended 
Well, I think the truth is Brian, nobody really knows, the problem with this exploit is it was completely silent, and I think as many people were completely unaware of it - including the bad guys. It is also not a trivial hack, and you would need to know what your doing. This would mean that people who were going to do it, would go after the big fish first.
All the main sites are being upgraded rapidly, and some were never affected in the first place, as they weren't using the exposed versions.
It is also a great time to update your passwords anyway - once you have checked the site is updated - using very strong passwords - especially your bank sites.
Please switch to using LASTPASS or Keypassx and generate some passwords you don't have to remember, and keep them safe on your machine. Most of my passwords are 25 characters long - where the site supports it. Makes them extremely difficult to crack.
You have to remember , this has been around for at least 24 months, so if they were going to strike you, they would have done it by now.
All software has bugs, and using Internet explorer in XP now without any security support at all, would be a much bigger threat. The hackers have been waiting for this moment with XP.
Brian, these is no need to panic keep calm ;-) - the exploit has been out in the wild for a long time and the damage has already been done. As Katherine mentioned I have been extremely busy working with Industry people to fully identify and understand the depth of the problem. It is basically a memory leak on some implementations of certain versions of openssl. If you are using an older version of the openssl library your not affected at all, it is only versions 1.0.1a-e and 1.02beta.
To check your version run this command in a terminal
openssl version
Now, all distributions are/have rushed out fixes for this problem, and all you need to do is use your package manager to update to the latest version of the code.
INFO for web site owners with SSL certificates
Now , if your run your own website, and offer secure logins over ssl/tls - then you must get a new certificate from your supplier and apply it to your server immediately. You must assume the old one has been exploited - there really is no way to check - so you must assume it has.
Also force all current ssl connections to timeout, so they have to re-connect to the new certificate.
Then get all your users to change their passwords - please everyone use LASTPASS or KeypassX - they generate really strong passwords.
GENERAL users across the web
Now everyone else needs to start using the advanced features in Firefox and Google chrome - not sure if IE offers this same feature. When you visit a site use HTTPS, this means you are connecting over SSL, and all modern browsers will show a green icon on the address bar. You can right click on this and look at the details. Now, before you rush to change any passwords on any sites, check this site has updated it's SSL certificate to anything later than 8th April. Then go in and change your passwords.
In all likelihood as many people have commented, most users have not been affected , so this is just a precaution. Again, please use something like LASTPASS or KEYPASSX to generate strong passwords, and different ones for every site you use.
Here are some helpful links to help you work out which sites I need to update etc.
Lastpass built in new heartbleed checker
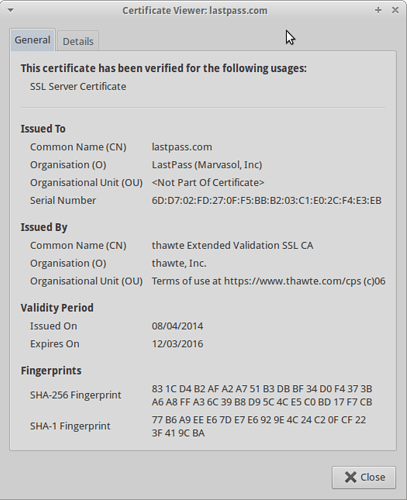
Below is a good certificate. If you need further help then put a comment in the forum.